Microsoft is going to drop out Windows XP from its service from next month, and about 95 percent of the ATM's all over the world will get effected by this, as All ATM's machine runs on Microsoft Windows XP. This is will be the major problem for all the Banks worldwide. Some of the Banks have decided to pay sum of the amount to Microsoft to keep the security update. But India is the only country who is migrating from Windows to Linux, and applying their own developed Linux distro "BOSS" to ATM's through out the country.
As usual ATMs are in the target of cyber criminals from a long wide, and once again hackers have found the new way to get the pay from the ATM in a illegal way. According to the Symantec, hackers have found a way to steal money from ATM's using a text message. This attack was first noticed by the firm in late last year, when the attacks were happening in Mexico.

On Monday, Symantec made a post which stats that Firm have noted a new malware called Backdoor.Ploutus. The Ploutus malware allows attackers to send an SMS message to a phone that is attached to an ATM. The ATM will then spit out the amount of money requested.
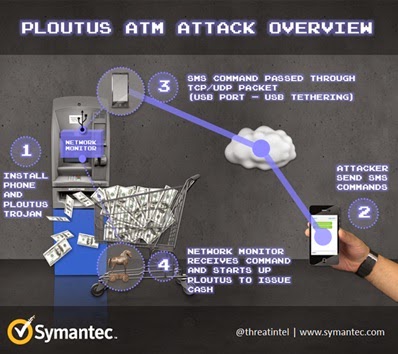
Symantec explains "The attacker first needs to upload the Ploutus malware to the ATM using either aUSB drive or a CD-ROM. Once Ploutus has been uploaded, the attacker also needs to attach a cell phone to the ATM using USB tethering. This allows the ATM and the cell phone to share an Internet connection while simultaneously charging the cell phone. The attacker then needs to send the attached cell phone two SMS messages. According to Symantec, the first “must contain a valid activation ID in order to enable Ploutus in the ATM” and the second “must contain a valid dispense command to get the money out”. The Ploutus malware will then tell the ATM to dispense a preset amount of money, which is then picked up by what Symantec calls a “money mule”.
To prevent this attack, Symantec recommends to update the operating system from XP to Latest version. Apart from this, physical security also to be taken, as attacker cannot be done entirely remotely. Symantec also recommends full-disk encryption and preventing booting up from unauthorized disks or USB drives.
Watch Video about ATMs Malware attack: http://www.youtube.com/watch?v=53vjNDV4RAY&feature=youtu.be
As usual ATMs are in the target of cyber criminals from a long wide, and once again hackers have found the new way to get the pay from the ATM in a illegal way. According to the Symantec, hackers have found a way to steal money from ATM's using a text message. This attack was first noticed by the firm in late last year, when the attacks were happening in Mexico.

On Monday, Symantec made a post which stats that Firm have noted a new malware called Backdoor.Ploutus. The Ploutus malware allows attackers to send an SMS message to a phone that is attached to an ATM. The ATM will then spit out the amount of money requested.

Symantec explains "The attacker first needs to upload the Ploutus malware to the ATM using either aUSB drive or a CD-ROM. Once Ploutus has been uploaded, the attacker also needs to attach a cell phone to the ATM using USB tethering. This allows the ATM and the cell phone to share an Internet connection while simultaneously charging the cell phone. The attacker then needs to send the attached cell phone two SMS messages. According to Symantec, the first “must contain a valid activation ID in order to enable Ploutus in the ATM” and the second “must contain a valid dispense command to get the money out”. The Ploutus malware will then tell the ATM to dispense a preset amount of money, which is then picked up by what Symantec calls a “money mule”.
To prevent this attack, Symantec recommends to update the operating system from XP to Latest version. Apart from this, physical security also to be taken, as attacker cannot be done entirely remotely. Symantec also recommends full-disk encryption and preventing booting up from unauthorized disks or USB drives.
Watch Video about ATMs Malware attack: http://www.youtube.com/watch?v=53vjNDV4RAY&feature=youtu.be

